Know How to Stay Secure from Phishing and Spoofing in 2022
To stay secure from phishing and spoofing attacks, you must know how to avoid them. Here are some of the most common ways to prevent them. Read on to learn more about IP, extension, and Vishing. Learning about the common IP Addresses is essential and you can learn them via Router login. By 2022 rolls around, you should be able to protect yourself from all of them.
To stay secure from phishing and spoofing attacks, follow these steps:
Vishing
You’re not alone. Most of us have experienced spoofing or phishing attacks at some point. This fraud occurs online, through email, or on a website, and looks for unnaturally large banner ads, strange website layout, or cosmetic differences. You should also avoid making online payments from unfamiliar sources. To prevent spoofing attacks, ensure your email account is secure and use two-factor authentication (2FA).
The latest trends in phishing attacks are brand impersonation and deep fakes. These new tactics use the same basic techniques many scammers use to get personal information. Phishers will often use a familiar brand to lure victims into sending out unsolicited emails. Beware of Phishing and Spoofing attempts in Recruitment Services, as fake job offers and impersonated recruiters can steal your personal information and money. Many victims are elderly and unfamiliar with cutting-edge technology. Therefore, they’re easy prey for this type of scam. This attack is not just short-term; it can be a long-term project that could result in a massive loss of information.
Phishing
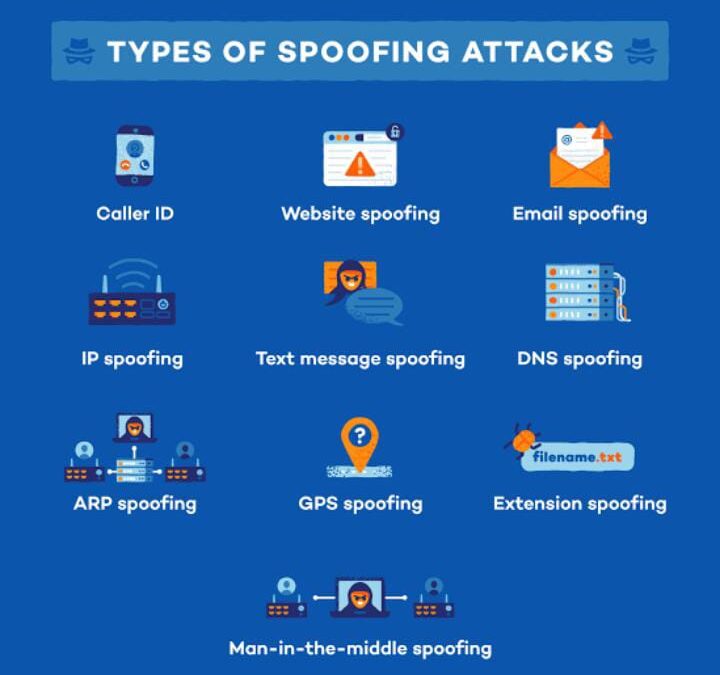
To stay secure in 2022, you’ll need to understand the different types of spoofing attacks and how to stay safe from them. Spoofing involves the use of fake identities and fake websites to trick users into divulging sensitive information. These attacks target your emails, social media profiles, and credit card numbers. These attacks are severe, so stay vigilant and protect yourself against them.
Email-based phishing attacks are rising, and many businesses and individuals rely on their email accounts to stay productive. Cybercriminals take advantage of this fact by targeting email users with sophisticated attacks that contain malware and manipulate their recipients. Attacks increase during the holidays and other significant events, and CISA warns against any cyberattack that can disrupt critical infrastructure. Following the tips below, you can stay secure against phishing attacks and be safe from spoofing and phishing attacks in 2022.
IP spoofing
In IP spoofing attacks, hackers use tools to alter a packet’s header and send it to a different computer. This creates the appearance that the package is from a reputable source, and the computer system receiving it accepts it. Because it happens at the network level, there are no visible signs that the packet has been tampered with. Therefore, it is hard to detect unauthorised boxes.
To prevent IP spoofing, web developers and companies should use two-factor authentication (2FA). This technology requires the victim to provide a second piece of information besides their password. The tools offered by secure password managers include USB tokens, biometric login, and temporary one-time passwords. Antivirus software can also provide tools to help users browse safely. Be wary of mobile app development offers disguised as phishing scams or spoofed websites to protect your sensitive data and avoid falling victim to malicious software. The right antivirus software can protect networked computers from spoofing attacks.
Extension spoofing
Extension spoofing is a significant security threat to keeping your data and computer safe. Extension spoofing can trick you into running malicious code, bypassing security controls. While most extensions are protected from malicious downloads, spoofing attacks can exploit these protections and use your system. Follow these steps to stay secure in 2022 and beyond. These steps are not only practical, but they are also free!
DNS spoofing
To stay secure from DNS spoofing and piling in 2022, it’s vital to implement DNS rewrite rules. This is a way to prevent DNS poisoning attacks from compromising your web connection. This attack is performed by using modified DNS records to spoof the destination address. DNS spoofing attacks aim to steal personal information or even trick a target into making payments.
A common way to stay secure from DNS spoofing and piling is to use a Virtual Private Network (VPN) service. A VPN provides a private, encrypted tunnel for web traffic. A personal DNS service uses an end-to-end encryption protocol to make servers more secure from DNS spoofing attacks. A VPN also makes your device’s DNS servers tougher to attack.
The Conclusion to Spoofing
If you have watched a movie, you’ve probably seen someone’s fingerprint copy. Although it might not be entirely convincing, it looks fantastic in the film. But what exactly is spoofing? It’s all about impersonation, disguise, and pretence. What’s more, it’s a highly effective way to get the attention of someone you want to impress. This article will explore a few ways you can spot a fake.
One common spoofing warning sign is an incorrect email address. These spoofs rarely look natural, so they should have mistakes or inaccurate information. A suitable red flag for a fake email is a request to validate the sender’s bank account or download an attachment. You should delete any such email as quickly as possible. This way, you’ll have no doubts about its legitimacy.
Another common tactic is to undertake a pair of spoofs going opposite directions. These spoofs usually make a profit per share equal to the spread, although this may not happen with every team. Instead, a spoofer may earn a small profit on each pair but may make millions in a short period. Software security must defend against both phishing’s deceptive tactics and spoofing’s fake identities to safeguard sensitive data and systems. However, the only issue with this method is that it discourages some people from participating in the market.
One of the most critical steps to take when defending against this type of attack is using encrypted websites. These websites should also be SSL-secured. An encrypted webpage has HTTPS:// in the address bar. That way, you’ll be able to trust the website and be confident that all the information you give is secure. If you’re worried about misusing your details, it’s time to stop spoofing. To know more about how to keep your monitor safe, Check out how to monitor your home network.