
AI and ML in Cybersecurity: Double-Edged Sword for Security and Threats
Introduction
Did you know billions of cyber attacks happen every day? Considering Microsoft, for instance. Their annual Digital Defense Report suggests that their clients experience more than 600 million nation-state attacks daily, including ransomware, phishing, identity theft, and many others. Unfortunately, with advancing technology and increasing attack surfaces and API integrations (as more and more applications move to the cloud), this number is only increasing.
This wave of rising cyber threats has made it clear: we need stronger, faster defenses, and that’s where AI and ML come in. These technologies have enabled intelligent threat prevention and detection, allowing cyber specialists to respond spontaneously and, in some situations, even before a cyberattack.
But there is a twist—AI and ML aren’t just being used for good. Cybercriminals rely on these technologies to make their attacks smarter and more complex, slipping past traditional defenses easily. Let’s explore the two sides of this coin in detail and find a balance to stay one step ahead.
The Current Cyberthreat Landscape
The digital world today is exposed to many different kinds of cyber attacks, ranging from ransomware to e-mail fraud. Below is a graphical breakdown showing the proportion of some common cyber attacks.
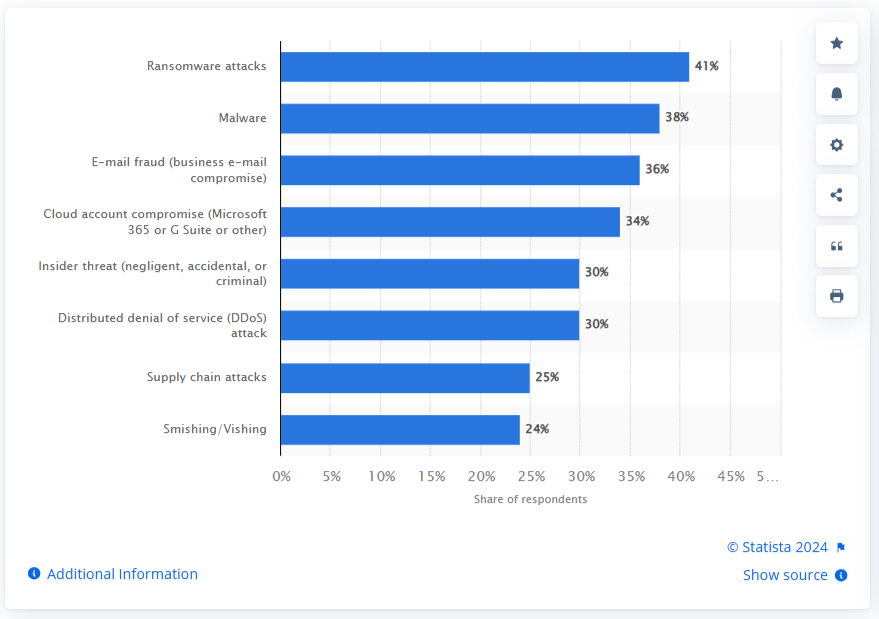
Ransomware attacks (a type of cyberattack where malicious software encrypts a victim’s data, blocking access until a “ransom” is paid to the attackers) constitute the largest segment. Additionally, 38 percent of respondents claimed malware (an attack where a system is corrupted to disrupt, damage, or gain unauthorized access to data, often for data theft) to be the second major cyber threat.
Another growing concern in the cyber threat segment is the increasing instances of digital arrest scams. These scams involve attackers pretending to be law enforcement or government officials, claiming that the victim’s digital assets have been involved in some illegal activities. The former then creates a sense of severity and urgency, pressuring the victim to make immediate payments without exiting the virtual call/meeting to avoid “arrest” or further legal action. In sudden response to such a grave situation, many people have paid thousands to clear their name.
In such a scenario, cybersecurity has become a top priority for most organizations today.
Read: Boost Device Speed with Digital Decluttering
What Else is Fueling the Increasing Need for Better Cybersecurity Solutions?
Rising Financial Implications of Cybercrime
Cybercrime costs businesses billions every year, from ransom payments to lost revenue. As per the FBI’s Internet Crime Report, over $12.5 billion was lost due to increased cybercrime complaints. And that’s just for the ones reported; imagine the total, including those that go unrecorded. These financial risks call for better AI cybersecurity solutions to defend against advancing threats.
Data Breaches Exposing Sensitive Information
Data breaches can leak sensitive customer and company data, leading to identity theft, fraud, and legal issues. Consider the recent Cisco data breach that occurred in October 2024. A malicious actor called “IntelBroker” claimed responsibility for holding sensitive information, such as GitLab projects, source code to several applications, and even customer SRCs. However, after conducting a thorough security audit, Cisco announced that the breached information was largely software artifacts, and none of its clients’ information was exposed.
Reputational Damage
Cyber incidents can severely damage your company’s reputation, especially if client information is compromised. If hackers successfully steal sensitive data, it not only invites potential legal and financial consequences but also creates a lasting negative impression on your customers. Even a single breach is enough to make them question your reliability, impacting retention and deterring new clients.
How Do AI and ML in Cybersecurity Make a Difference?
Traditional cybersecurity methods, such as implementing firewalls and intrusion detection systems, have been effective in protecting against known threats. They were built on pre-determined rules defined using age-old databases on malware signatures and other malicious activities. But with today’s unknown cyber threats, these approaches often fall short because of their inherent, reactive nature.
Today, cyber-attacks have become more dynamic. Attackers are always seeking newer ways to develop complicated malware strains and sophisticated phishing tactics that can surpass traditional security tools. Without the ability to “learn” from these changes, traditional security systems are often too late to respond.
But that’s not the case with AI and ML in cybersecurity solutions. Unlike traditional methods, these technologies take a proactive approach and examine volumes of threat data (malware signatures, IP blacklists, domain reputations, threat actor profiles, etc) in real-time, adapt to new patterns of behavior, and even predict possible threats before they occur.
AI in cybersecurity can help in:
- Spotting unusual behavior and flagging potential threats like unauthorized logins or unexpected data transfers before they escalate.
- Learning and adapting to new threats by recognizing patterns.
- Automating threat detection to identify threats faster and reduce the time attackers have to cause damage.
- Predicting future attacks to allow companies to strengthen defenses in advance, even before the actual attack happens.
- Filtering out phishing attacks to protect users from fake messages aiming to steal information.
- Monitoring traffic to keep an eye on network activity, quickly identifying any unusual behavior that might signal a breach.
The Flip Side of AI and ML in Cybersecurity: Making Attacks More Sophisticated
There is a flip side to integrating ML and AI in cybersecurity that cannot be ignored. Even cyber criminals are using them to level up their game. Let’s see how attackers are using AI and ML to make their cyber tactics more sophisticated:
- Advancing Phishing Scams
AI can be used to generate convincing fake emails or websites that are nearly identical to legitimate ones. Attackers can even imitate someone you know (and clone their voice); they can also pretend to be a bank service provider or a mortgage company, making it harder for you to differentiate.
- Developing Detection-Proof Malware
With ML in the picture, attackers can make malware adapt and change its code on the fly to avoid detection by traditional cybersecurity protocols. This means even malware can “learn” which antivirus signatures or firewall settings to bypass, increasing its chances of infiltrating networks unnoticed.
- Strategizing for Large-Scale Attacks
AI enables attackers to automate complex attacks, like Distributed Denial-of-Service (DDoS) attacks, at scale with minimal effort. It can also help them adjust the attack in real-time, maximizing the disruption and damage caused.
- Mimicking User Behavior
Attackers can use AI to mimic legitimate user behavior, making it easier to slip into systems without raising any alarms. By “camouflaging” as a regular user, they can bypass security that relies on tracking typical behavior patterns.
- Conducting Social Engineering Attacks at Scale
Attackers can use AI/ML-based analysis of social media profiles and digital footprints to build detailed profiles of targets. They can use this data to create highly personalized social engineering attacks, making scams more believable and hard to detect.
- Creating Deep Fake Content for Fraud
Generative AI has made it easier than ever to produce hyper realistic fake content. Cybercriminals are pushing boundaries by using it to create deep fake videos and audio that impersonate trusted individuals. With this technology, they can mimic a familiar voice or face to trick employees or executives into sharing sensitive information or approving transactions, making it harder than ever to tell real from fake.
A Synergistic Approach: Humans-in-the-Loop with AI and ML in Cybersecurity
AI and ML are a double-edged sword in the digital world. On the one hand, these technologies have brought significant efficiency improvements; on the other, they have also opened doors for more aggressive attacks. However, there is an approach that can help you find the right balance— humans-in-the-loop. Where certain cybersecurity solutions may not be able to identify adversarial attacks, expert human oversight can help you identify and flag subtle nuances that suggest malicious behavior.
- When even AI in cybersecurity misses insider threats, human oversight can spot context-based cues like unusual file access patterns.
- When AI struggles with false positives, humans can filter out unnecessary alerts by distinguishing real threats from harmless activity.
- When attack patterns evolve too quickly for AI systems in cybersecurity, human experts can devise new tactics and adjust defense strategies in real-time.
- When social engineering attacks slip through, human oversight can catch emotional cues, like manipulative language or tone, signaling a possible threat.
End Note
Advancing technologies like ML and AI in cybersecurity is both a boon and a bane. On one hand, these technologies have fueled a connected, digital world where threats can be detected faster than ever. But on the other, they’ve opened doors for cybercriminals to launch more sophisticated attacks than we’ve seen before. To tackle this double-edged sword, a humans-in-the-loop approach can make a big difference. By pairing AI cybersecurity tools’ efficiency and precision with human intuition and experience, you can strategize for a defense that’s smart and adaptable.
If off-the-shelf AI solutions do not meet your specific requirements, you can also explore custom-fit AI/ML development services. These service providers can configure a personalized AI cybersecurity solution to address the specific issues you face, be it malware, man-in-the-middle (MitM) attacks, or denial-of-service (DoS) ones. The idea is to bring technology and human expertise together, which is your best bet for staying a step ahead and keeping the digital world safe.